Why are Digital Signatures hard to forge? Vulnerabilities of Digital Signatures
Digital Signature with Its basically an asymmetric cryptographic procedure that makes use of public and private keys generated by an algorithm, makes it extremely difficult to forge; The private key is only known by the signatory, and is stored on their own device or in the cloud for centralized signatures. This feature is essential to prevent forgery. But does Vulnerabilities of Digital Signatures
The public key is then shared with the recipients of the digital signature. The procedure for creating a digital signature goes as follows:
The algorithm outputs the private key and a corresponding public key, a signing algorithm then, given a message and a private key, produces a signature, which is encrypted by the private key itself (so the digital signature cannot be forged without access to the private key). A signature or document verifying algorithm that, given the message, public key and signature, either accepts or rejects the message’s claim to authenticity.
Vulnerabilities of digital signatures
However, digital signatures in the age of ever more powerful computers and knowledge about cryptographic concepts, can be vulnerable to some exploits. Unfortunately, as cyber-criminals become more adept at discovering vulnerabilities within information systems, they have discovered methods to launch e-signature validations attacks. Here are three classes of e-signature validation attacks that allow hackers to take advantage of certain vulnerabilities that may exist within some e-signatures.
It is important to note that each attack takes advantage of a missing step within the signature verification process and not on the signature generation. As we will note in the end, if a signature format conforms to the referenced standards, these signature verification algorithms can be produced which are immune to the mentioned attacks.
These Vulnerabilities of Digital Signatures typically include:
- hackers obtaining the private keys used to sign messages or documents
- the manipulation of the signing procedure
- affecting the presentation of the message or document (i.e. by a malicious actor ensuring that a signer sees something different from what they intend to sign).
- The increased focus on the use of digital signatures during the COVID-19 pandemic is sure to have identified a raft of problems — and, naturally, solutions are sure to have been developed. [5]
The E-Signature specific vulnerabilities described below are based on a publication by pdf-insecurity.org.
E-Signature Attack #1 – Universal Signature Forgery (USF)
The goal of a Universal Signature Forgery (USF) attack is to disable the e-signature verification process by manipulating the signature object by adding invalid content to it or removing references to the signature object. This object holds all the information that is needed for signature validation.
Even though the signature object exists and remains within the e-signature, its validation logic is unable to apply the correct cryptographic operations needed to verify the signature because the USF attack has confused the signature validation logic. If the hacker is successful with their USF attack, the online validation logic or view application will display that the e-signature is valid and belongs to a specific individual or entity on its display panel.
E-Signature Attack #2 – Incremental Saving Attack (ISA)
In the instance of an Incremental Saving Attack (ISA), the goal is to make an incremental save to a document by redefining its structure. Therefore, the target of this attack is a PDF document’s incremental saving or incremental updating feature, which when used legitimately allows a user to add annotations to their PDF. These annotations are saved incrementally as a new PDF body after the PDF’s original content. The incremental saving feature is also used for signing the PDF and allows for the signature object to be appended to its original file content.
Normally, any alterations after a document has been signed would trigger a warning that the document had been tampered with. However, when conducting an ISA attack, the attacker might add additional content, such as new pages or annotations to an already signed PDF. Technically, this breach is not attack. Instead, it is an exploit of the PDF’s incremental saving feature. However, the vulnerability takes place when the signature’s validation logic does not detect that the content within the PDF file has been tampered with. The unsigned content that has been added after the signing of the document is simply seen as an update by the individual or entity that originally created the document’s e-signature. A successful ISA attack will result in new content/body updates being shown, while signature verification processes will remain unaware that modifications or updates have been made to the PDF document.
E-Signature Attack #3 – Signature Wrapping (SWA)
A Signature Wrapping (SWA) attack uses a unique approach to bypass a PDF’s signature protection without accessing its incremental saving feature. It does thing by moving the second part of the signed /ByteRange to the end of the breached document. Meanwhile, the attacker then reuses the xref pointer within the document’s signed trailer to reference his manipulated xref. In some instances, the attacker may also wrap the relocated second part with a stream object or dictionary to prevent it from being processed by the PDF’s or the online signature protection feature.
In a successful SWA attack, an attacker can add malicious unsigned objects into the document. If he has chosen to wrap the relocated second part, these objects can be placed before or after the manipulated xref. If no wrapping is added, the malicious objects would be placed after the manipulated xref. Depending on the PDF viewer, the attacker may copy the file’s last trailer and place it after his manipulated xref to allow the PDF file to be opened and to bypass signature verification without the manipulations to be detected.
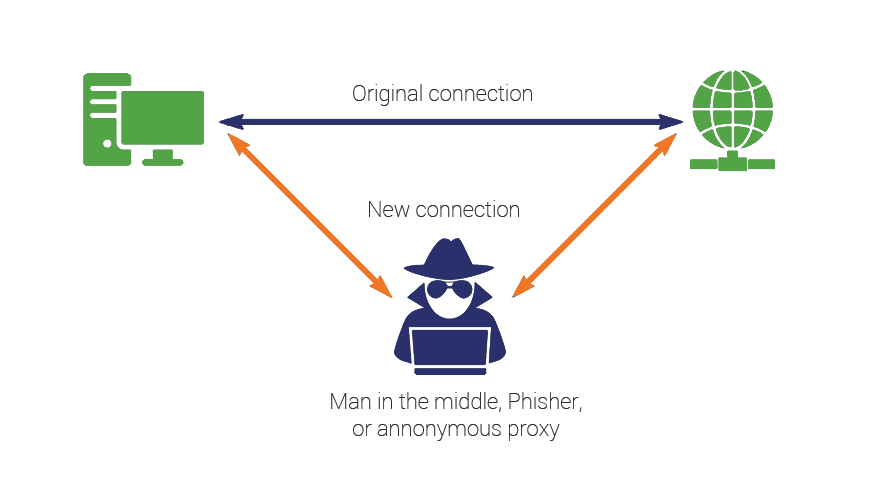
Man-in-the-Middle (MITM) attack
A MITM attack happens when a communication between two systems is intercepted by an outside entity. This can happen in any form of online communication, such as email, social media, web surfing, etc. Not only are they trying to eavesdrop on your private conversations, they can also target all the information inside your devices.
Taking away all the technicalities, the concept of an MITM attack can be described in a simple scenario. Imagine being brought back to the days of old when snail mail was rife. Jerry writes a letter to Jackie expressing his love for her after years of hiding his feelings. He sends the letter to the post office and it’s picked up by a nosy mailman. He opened it and, just for the hell of it, he decided to rewrite the letter before delivering the mail to Jackie. This results in Jackie hating Jerry for the rest of her life after “Jerry” called her a fat cow. The moral of the story is the mailman is a jerk, and so are hackers.
A more modern example would be a hacker sitting between you (and your browser) and the website you’re visiting to intercept and capture any data you submit to the site, such as login credentials or financial information.
How Does a Man-in-the-Middle Attack Work?
In the realm on protecting digital information, a man-in-the-middle (MITM) attack is one of the worst things that can happen to an individual or organization. MITM attacks happen when an unauthorized actor manages to intercept and decipher communications between two parties and monitors or manipulates the exchanged information for malicious purposes. And while the term has been a staple in cybersecurity circles, new and sophisticated versions are continuously appearing, able to hurt the heart of corporate IT systems.
For instance, hackers can stage MITM attacks to steal sensitive data, such as account credentials or credit card information, or they can use them to deliver malware-inflicted files and applications while posing as legitimate sources.
During an MITM attack, each of the legitimate parties, say Alice and Bob, think they are communicating with each other. But in reality, their exchanges are going through Eve, the eavesdropper, who stands between them, posing as Alice to Bob and as Bob to Alice. Eve can decide to change the information before passing it on from Alice to Bob, or she can just sit there and silently record their exchanges for future use.
Man-in-the-middle attacks come in different forms. Conceptually, they’re similar, but technically, they’re different and they leverage various vulnerabilities in security practices. Here’s a breakdown of different types of MITM attacks and how you can protect yourself against them.
Other forms of MITM attack
Man in the Browser (MITB)
Man-in-the-browser is a form of man-in-the-middle attack where an attacker is able to insert himself into the communications channel between two trusting parties by compromising a Web browser used by one of the parties, for the purpose of eavesdropping, data theft and/or session tampering.
Man-in-the-browser is often used by attackers to carry out various forms of financial fraud, typically by manipulating Internet Banking Services.
In order to compromise the browser, adversaries can take advantage of security vulnerabilities and/or manipulate inherent browser functionality to change content, modify behavior, and intercept information. Various forms of malware, most typically malware referred to as a Trojan horse, can be used to carry out the attack.
Session Hijacking
Session hijacking, also known as cookie side-jacking, is another form of man-in-the-middle attack that will give a hacker full access to an online account. When you sign into an online account such as Facebook or Twitter, the application returns a “session cookie,” a piece of data that identifies the user to the server and gives them access to their account. As long as the user’s device holds on to that session token, the server will enable them to use the application.
IP spoofing
Hackers use IP spoofing in a number of different ways, including staging DDoS attacks, in which attackers drain the resources of a server by flooding it with bogus network traffic. IP spoofing can also be used in man-in-the-middle attacks. In this case, the attacker stands in between two communicating parties, spoofing each of their addresses to the other. This way, each of the victims sends their network packets to the attacker instead of directly sending it to its real destination.
The biggest defense against MITM attacks conducted through IP spoofing is to use encrypted communications. When the information between two parties is encrypted with a key that only they hold, it will make sure that even if a malicious party manages to intercept the traffic, they won’t be able to read or manipulate its contents. Authenticating user identities also prevents hackers from gaining unauthorized access to network resources by simply spoofing their IP address.
SSL stripping
Another form of man-in-the-middle attack happens when a hacker manages to stage an SSL stripping scheme against the victim. As we mentioned previously, hackers can’t break into legitimate HTTPS traffic between a client and a server even if they manage to intercept and relay the communications.
In the case of SSL stripping, the attackers downgrade the communications between the client and server into unencrypted format to be able to stage a MITM attack.
Another measure to protect against SSL stripping is to make sure your local network is secure and unauthorized parties don’t have access to it. SSL hijacking requires access to your local network. At the corporate level, setting up strong firewalls will also prevent outside parties from gaining access to your local network and moving laterally to stage MITM attacks.
Wi-Fi eavesdropping
Also known as an “evil twin” attack, hackers perform Wi-Fi eavesdropping is a type of man-in-the-middle attack that tricks unsuspecting victims into connecting to a malicious Wi-Fi network. To perform Wi-Fi eavesdropping, a hacker sets up a Wi-Fi hotspot near a location where people usually connect to a public Wi-Fi network. This can be a hotel, a restaurant or your local Starbucks. The hacker then names the hotspot after the actual public network that people use in that location (thus the name “evil twin”).
One of the most important measures is to disable automatic Wi-Fi connections and make sure you manually select which networks you want to use. It will be a little less convenient, but at least you’ll have a greater chance of avoiding evil twins and MITM attacks.
Another very important protective measure to prevent MITM through Wi-Fi eavesdropping is to use a virtual private network (VPN). VPNs create a secure channel for all your internet traffic, encrypting everything and sending them through an intermediate server. When using a VPN, even if a hacker manages to intercept your communications, all they will see is a stream of encrypted data, and they won’t be able to make sense of it. They won’t even be able to figure out which sites you’re browsing to, so they won’t be able to redirect you to their own malicious copies of the websites.
eIDAS Standards and Enhanced Protection Against E-Signature Attacks
The eIDAS referenced standards include requirements which goes beyond the minimum requirement for PDF signatures. With these additional requirements, signature verification algorithms can easily be implemented to thwart attacks that would otherwise go unnoticed through normal PDF or online signature verification processes. eIDAS provides guidelines for the use of advanced electronic and qualified electronic signatures that add to the protections that are available within PDF software. Under the eIDAS legislation, all EU member states are required to recognize the validity of qualified and advanced electronic signatures that comply with its set standards.
Advanced electronic signatures must meet certain requirements that ensure their authenticity in order to be considered valid. The signature must be able to identify and be uniquely link to its signatory.
The signatures must be created with electronic signature data that is under the sole control of the signatory. Additionally, that electronic signature data must be able to identify if any tampering of data has occurred after the signature has been created.
The integrity of a qualified e-signature can be assured when it meets all eIDAS requirements and is based on a qualified certificate issued by an EU member state. Qualified electronic signatures are validated with certificates that have been issued through a qualified trust service provider. That provider must verify the signer’s identity before issuing a certificate.
A potential successful attack on the validation of a signature can depend on how the signature is created as well as how stringent the validation process is. Because of the nature of standard PDF software and its updating features, it leaves e-signatures vulnerable to attack. But these vulnerabilities can be mitigated by adopting the eIDAS referenced standards for Advanced or Qualified Electronic Signatures.
Gathered and Revised: Forough M.Salehi
Source: 1. Paco Wright,july 23 2020
Source: 2. Ricky Publico, March 1 20171.
Source: 3. Shimrit Tzur-David, August 8 2020
Source: 4. Chris Alen, Steve Manhill, Digital Signature for dummies
Source: 5. Terence Broderick, April 29 2021